
Passwords are critical for protecting important accounts, but they are subject to a variety of threats, including phishing and malware. Given these vulnerabilities, relying exclusively on passwords is insufficient for security. That’s where 2FA comes in, offering an extra layer of security. It strengthens security, making it more difficult for attackers to access your data and systems. While some may be hesitant to set up 2FA because of to its supposed annoyance, it is not only an option, but a requirement in today’s digital landscape.
Two-Factor Authentication (2FA) is an additional security measure that is used after entering your password to protect your accounts from unauthorised access. By requiring two forms of verification, 2FA makes it significantly harder for cybercriminals to breach your systems and steal your data. Even with 2FA, your business should still create strong passwords, by making them complex, long and unique.
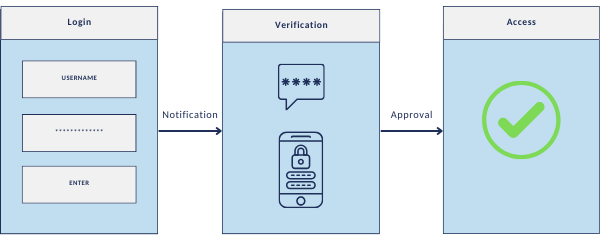
For stronger 2FA authentication, choose authenticator apps or SMS over email because they are more secure, and consider employing external off-net devices such as mobile phones for added protection.
2FA authenticator apps provide a convenient and effective way to bolster security by requiring both something the user knows (password) and something that’s generated dynamically (authenticator app) for authentication.
SMS two-factor authentication validates the identity of a user by texting a One-Time Password (OTP) to their mobile device. It is the most common and simplest form of 2FA implementation.
The system sends an OTP or verification link to the user’s email address for second-layer authentication. While effective, using SMS or an Authenticator App is safer due to known vulnerabilities in email platforms.
